In this section, I post articles explaining the software and artificial intelligence concepts in a simple way
Take a look at some of my posts
In this section, I post articles explaining the software and artificial intelligence concepts in a simple way
Take a look at some of my posts
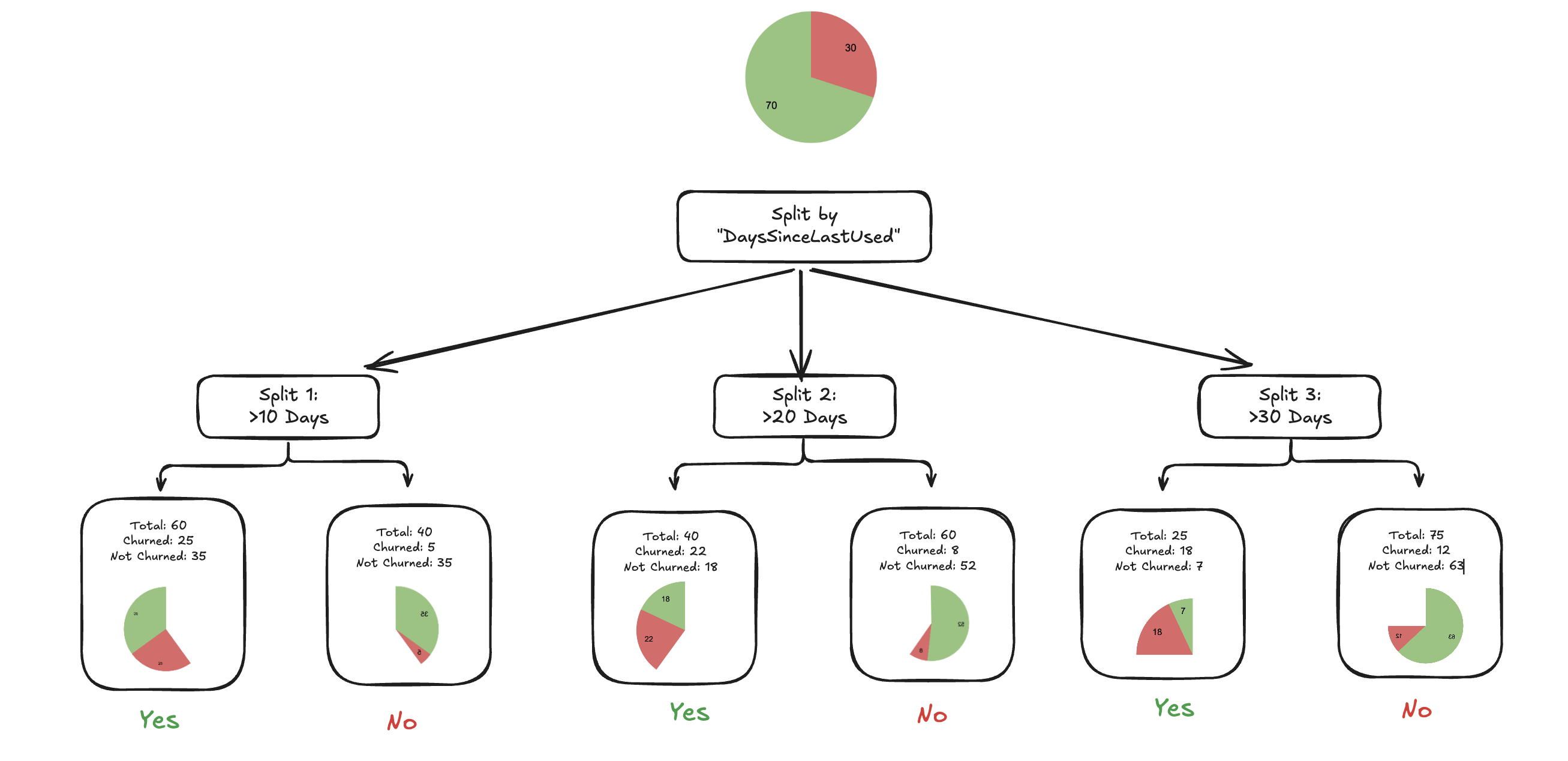
How Decision tree works, the basics - split, gini, entropy, information gain
Ever wonder how your email app just knows what spam is? Or how Netflix uncannily suggests the exact B-movie you were secretly in the mood for? The answer is Machine Learning (ML). Before ML, software was a bit of a bureaucrat. You had to write explicit, rigid if-this-then-that rules for every single possibility. This works fine until the real world, in all its messy glory, shows up. ML flips the script. Instead of feeding a machine rules, you feed it examples. The machine’s job is to look at thousands or millions of examples and figure out the patterns on its own. ...
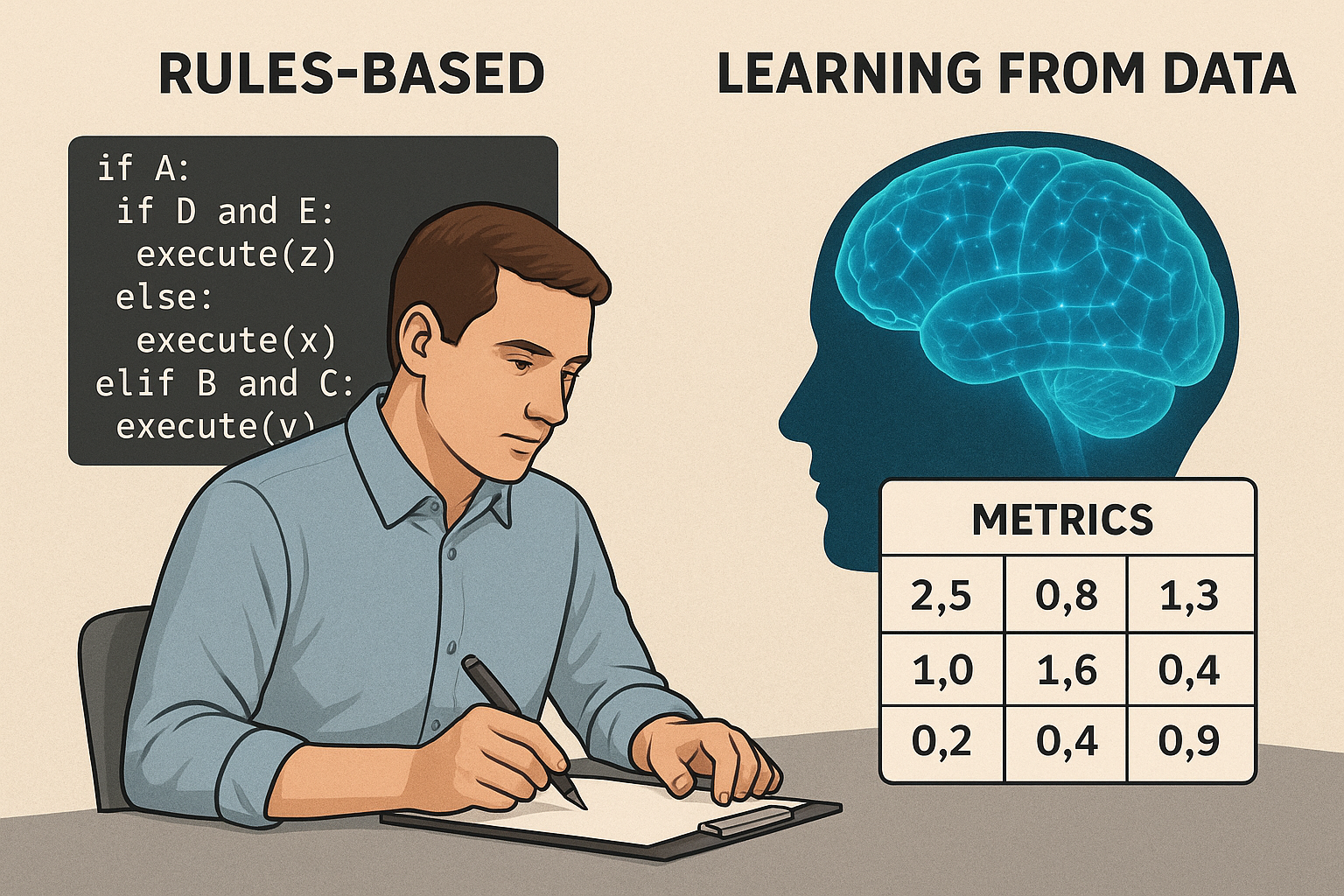
Part 1 of “AI ain’t Magic, It’s Math” Before AI became what it is today, machines behaved like bureaucrats: they only did what you explicitly told them to do. Software was ==Rules Based==. Meaning: you wrote conditions, and the machine reacted to those conditions. First you create the rules mentally If A happens then X, If B and C happends then do Y, If A and D and E Happens then Do Z Then hard code it ...

..coming soon
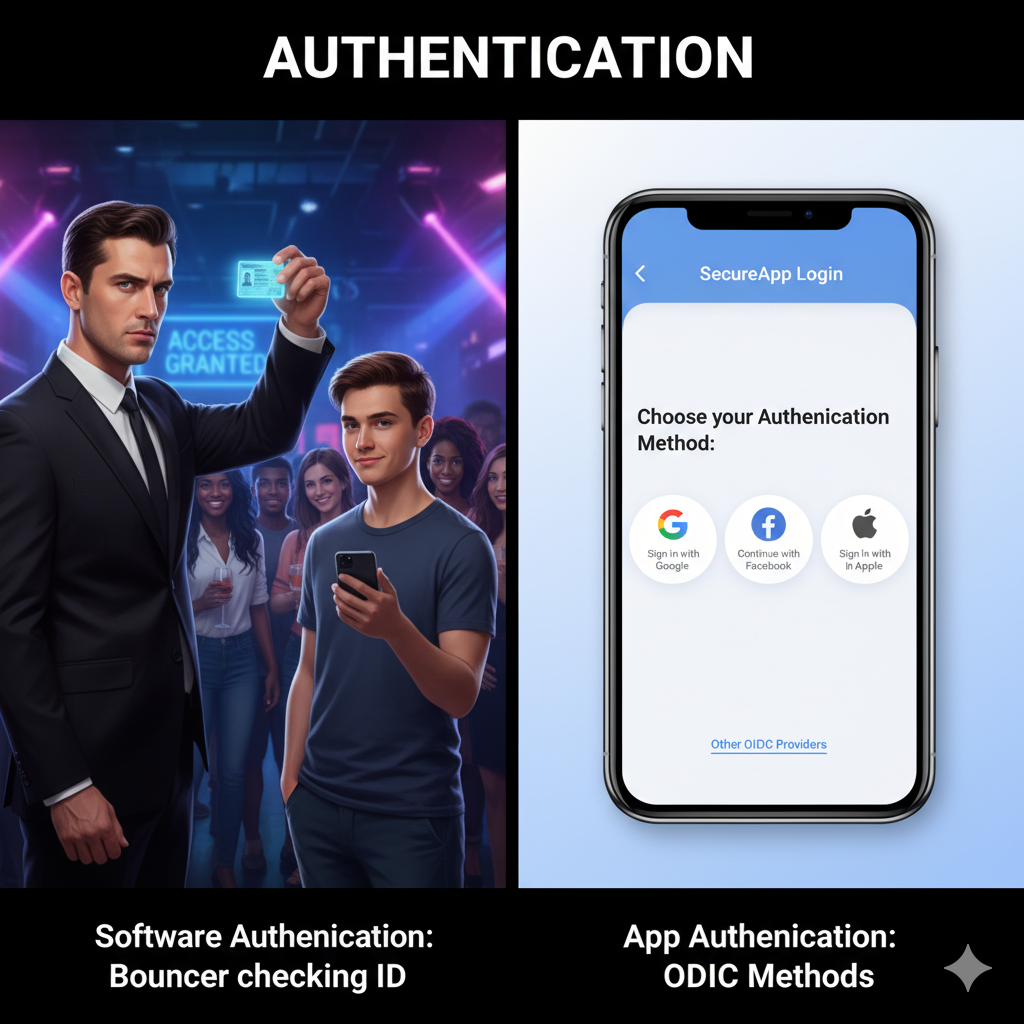
You hear these two words thrown around all the time, and they’re almost always used together. But here’s the thing: they do two completely different jobs. Getting them right is the foundation of all digital security. So what’s the deal, exactly? Authentication is the bouncer at the club door checking your ID. Its only job is to answer one question: “Who are you?” Authorization is the VIP wristband you get after you’re inside. It tells the bouncer which rooms you’re allowed into. Its job is to answer: “What are you allowed to do?” Authentication always comes first. You can’t figure out what someone is allowed to do until you know who they are. That’s it. One proves your identity, the other checks your permissions. Let’s break down the most common ways apps do both. ...